An IP phone uses Voice over IP technologies allowing telephone calls to be made over the internet instead of the ordinary PSTN system. Voice over Internet Protocol is a protocol optimized for the transmission of voice through the Internet or other packet switched networks.
The most attractive part of implementing such a system is the lower calling cost. When calling other IP phones over the internet one pays for the fixed cost of internet bandwidth. Therefore IP phones are widely used in making international calls in Call centers and other business organizations.
All you need to do is to get an IP phone adapter from your VoIP service provider and that’s it. The good thing about using IP phones is that you do not need any special equipment to make it work, just the adapter. When you use IP phone systems, it works with an Ethernet port (or also called RJ-45) rather than using a regular wall phone jack. When use your IP phone service to make calls, your digital IP phone will connect through your broadband Internet modem.
Advantages of VoIP:
If you have a broadband connection with either DSL or cable, then you can use VoIP to make low cost calls. For a PC-to-PC phone call it can even be no cost to any other computer anywhere in the world (that has VoIP service installed as well, of course). Skype, Gtalk and Yahoo messenger provides this service. While there is usually a cost to make a PC-to-phone connection, it is usually less than a “traditional” long distance call.
Many VoIP service providers will charge a monthly fee allowing you to make unlimited calls within a specified geographical area, with a nominal extra charge for calls outside that set area. VoIP provides the advantage of portability if you are a traveler, you just have to sign in to your VoIP service wherever you are and make the call.
This portability is available for phone-to-phone VoIP service as well. Your VoIP service provider will provide you with an internet phone number that follows you wherever you go.
Services like call forwarding, call waiting, voicemail, caller ID, three-way calling and more are available through your IP phone, usually at no extra charge. You can also send data, as you would expect with a broadband internet connection, like pictures and documents, all while talking on the phone.
Disadvantages of VoIP:
The biggest problems of VoIP are power interruptions, quality of service and reliability.
The normal phones are not powered by your power line and thus they work when you have a power outage. These phones are powered by the phone line itself. This isn’t the case with an IP phone. If the power goes out, then there is nothing to power your internet connection or your IP phone.
There are also issues with VoIP sound quality and reliability. Just like any data sent over the internet, it is sent through the network scrambled into “packets”. Email and other documents sent over the internet are easily “reassembled” at the other end for a seamless transmission. Due to the real-time nature of voice communication, this reassembly process becomes more of a problem with VoIP. In order to minimize the delay of the voice connection, some data packets may occasionally need to be “dropped” if they don’t arrive in time, resulting in short periods of silence in the audio stream.
The amount of dropped data depends on the distance and speed of the connection. High traffic networks may experience more dropouts, especially at times of peak usage. One workaround that service providers can use is to create dedicated data paths for audio transmission.
I’ll explain about the popular 7940 series Cisco IP phone and how it is configured in another post.
Cheers ;)















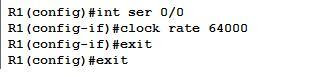














 Now we have to save this configuration in the NVRAM, so that in case you have to reboot the router, the configuration is not erased. For this, you can use ‘Write’ of ‘copy running-config startup-config’. This procedure can be anytime while configuring also.
Now we have to save this configuration in the NVRAM, so that in case you have to reboot the router, the configuration is not erased. For this, you can use ‘Write’ of ‘copy running-config startup-config’. This procedure can be anytime while configuring also.
 1 - Handset light strip: Indicates an incoming call or new voice message
1 - Handset light strip: Indicates an incoming call or new voice message
